Recorded Futures Insikt Group identified a 76% increase in publicly reported data breaches from 2022 to 2023. While 2024 data is not yet complete, Recorded Future data on validated data breaches project a further 5% increase in 2024 compared to 2023. The scale of this increase in the past two years invites a sense of urgency and concern, especially when the attack surface for data breaches is moving further out of companies control. Based on what we can measure, the costliest impacts of data breaches in the last several years have been operational disruption, legal risks, and declining sales due to churn and loss of customer trust. However, the real risk lies in companies falling behind in their security strategy and failing to adopt a new way of thinking. Our immediate and long-term solutions provide a starting point for effectively addressing this escalating threat.
Data Breaches Are on the Rise
- The industries most affected by the 76% increase in data breaches in 2023 were the healthcare, finance, information technology and software, insurance, and manufacturing sectors.
- The insurance sector saw the largest increase in reported data breaches in 2023, with a 178% increase. This was followed by healthcare with a 107% increase and manufacturing with an 81% increase. The sensitivity of these industries data and the cost of disruption to their operations have likely been driving factors for threat actors to target these industries.
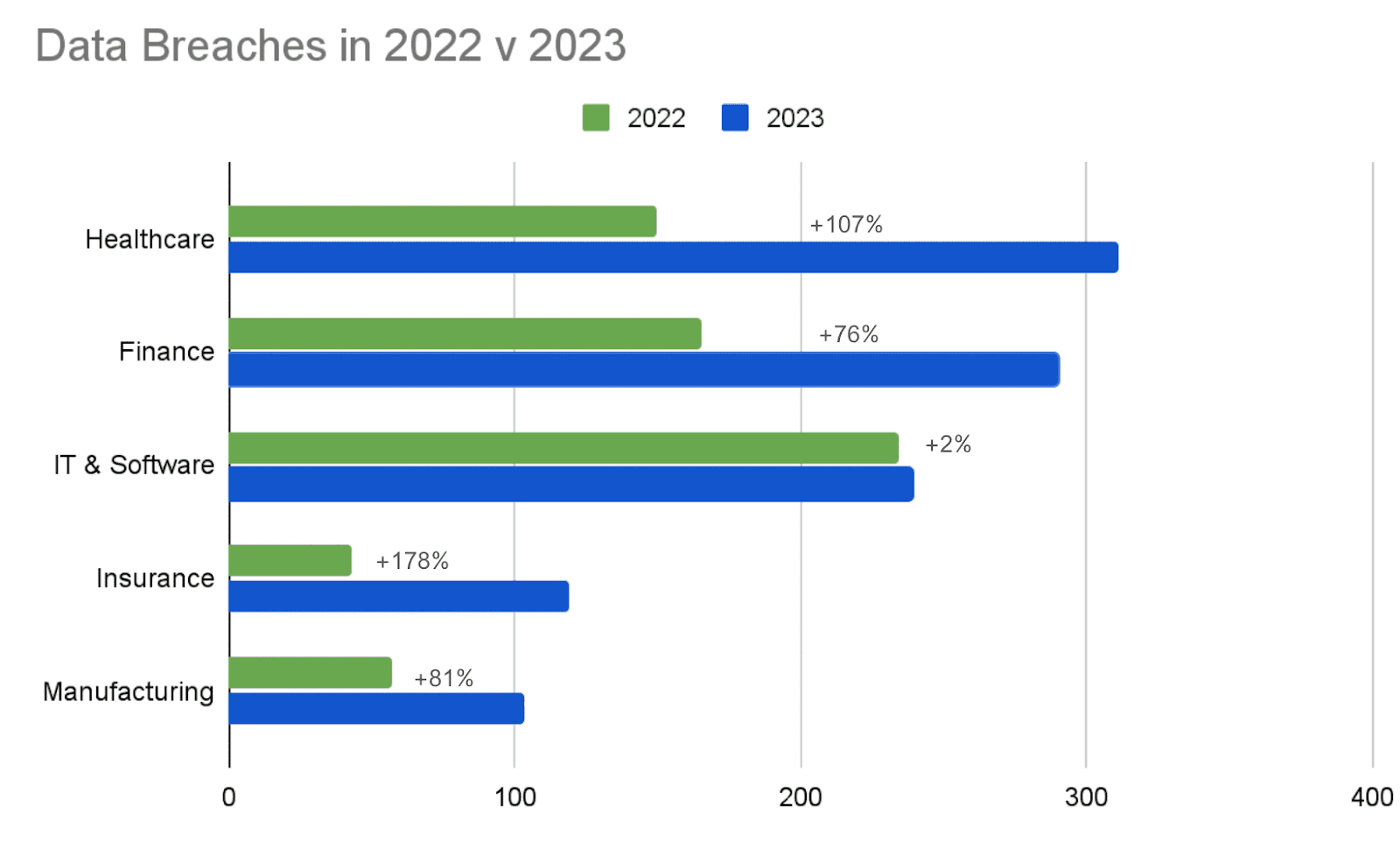 Figure 1: Publicly reported data breaches in the top five affected industries In 2022 compared to 2023 (Source: Recorded Future)
Figure 1: Publicly reported data breaches in the top five affected industries In 2022 compared to 2023 (Source: Recorded Future)
The Costs of Data Breaches Continue to be High
- Research from IBM shows that the average total cost of a data breach reached an all-time high in 2024 of USD 4.88 million.
- The business impacts of data breaches are often easiest to measure right after a breach is detected, such as the four-day outage at an Australian personal loan provider in early 2023 that resulted in what we estimate could have been a revenue disruption of over $6 million USD while security teams mitigated the breach.
- However, impacts can also linger: In Q4 of 2023, after a US genetics testing company confirmed it had been hit by a major data breach, it saw decreased sales and underperformed the Nasdaq by approximately 16%. While it was not the only factor at play, the negative media coverage around the data breach is highly likely to have played a role in stock, sales, and revenue underperformance, especially when considered in the context of the extensive literature indicating how cyberattacks can negatively impact stock prices.
The Causes Are Moving Further Out Of Control
- As the costs of a data breach increase, the causes of breaches are also moving further out of organizations control. Companies may have robust vulnerability remediation on their infrastructure and devices, but threat actors are increasingly looking for vulnerabilities in third-party software to gain access to more potential victims1. Third-party software providers are critical components of the software supply chain and may not have effectively identified or addressed these vulnerabilities. This lack of remediation exposes the entire ecosystem to heightened risks of compromise, as reliance on third-party software expands the attack surface.
- As more and more data is likely hosted on third-party cloud providers, threat actors are abusing exposed administrative accounts (Valid Accounts) to gain privileged access and exfiltrate data more effectively. Recorded Futures 2023 Annual Report highlighted a 22% increase in validated cyberattacks leveraging the Valid Accounts technique. Based on initial analysis of 2024 data, threat actors continue to abuse valid accounts at various stages of an attack sequencesuch as discovery, privilege escalation, and defense evasionto facilitate data theft. These accounts enable lateral movement within networks to access sensitive systems, facilitate reconnaissance by appearing as normal user activity, and help blend into regular traffic to avoid triggering security alerts.
Getting Ahead of the Problem
One immediate action security teams can take to improve their organizations risk profile is to create a vendor catalog to identify all external parties with access to company data. Use of risk management software, such as Recorded Futures Third-Party Intelligence Module, enables extended visibility across the entire third-party ecosystem to uncover risk exposures and prioritize risk mitigation.
More long-term actions can also be helpful in mitigating the chances or severity of a data breach:
- Tokenization or encryption helps to render sensitive data meaningless or inaccessible, respectively, outside of a secure environment. Organizations can reduce exposure to risks associated with storing sensitive data and maintain compliance with data privacy laws and regulations by implementing the appropriate method. An audit of necessary tasks associated with data, and not just the sensitivity of data itself, can help with applying the principle of least privilege effectively.
- Close collaboration between multiple teams forensics, incident response, and legal and compliance can more successfully manage the fallout from potential data breaches. If these teams do not already have a good working relationship, chances are low that they will automatically have one in response to a severe and public data breach. As a result, it is a good idea for these teams to know each other well outside of a crisis.
1 Sources: H1 2024: Malware and Vulnerability Trends Report, Recorded Future Ransomware Solution, Verizon 2024 Results and Analysis
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/blog/business-impact-data-breaches