In a recent cybersecurity breakthrough, researchers have unveiled significant updates to the HijackLoader malware, a sophisticated modular loader notorious for delivering a variety of malicious payloads. The malware has been updated to deploy threats such as Amadey, Lumma Stealer, Racoon Stealer v2, and Remcos RAT, showcasing an alarming versatility in its operations. HijackLoader has evolved […]
The post HijackLoader Malware Attack Windows Via Weaponized PNG Image appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
In a recent cybersecurity breakthrough, researchers have unveiled significant updates to the HijackLoader malware, a sophisticated modular loader notorious for delivering a variety of malicious payloads.
The malware has been updated to deploy threats such as Amadey, Lumma Stealer, Racoon Stealer v2, and Remcos RAT, showcasing an alarming versatility in its operations.
HijackLoader has evolved to incorporate a novel technique involving using a PNG image to decrypt and initiate the loading of subsequent stages.

This method is part of a broader strategy that includes dynamic API resolution, meticulous blocklist process checking, and evasion of user mode hooks, highlighting the malware’s increasing sophistication in avoiding detection.
The updates also introduce new modules designed to enhance the malware’s functionality. These include capabilities for creating processes, bypassing User Account Control (UAC), adding exclusions to Windows Defender, and writing files, thereby expanding the malware’s ability to compromise and control infected systems.
Detailed analysis of HijackLoader’s operational stages reveals intricate technical mechanisms.
The first and second stages of the malware involve complex loading processes, module utilization, and injection methods, underscoring the advanced nature of this threat.
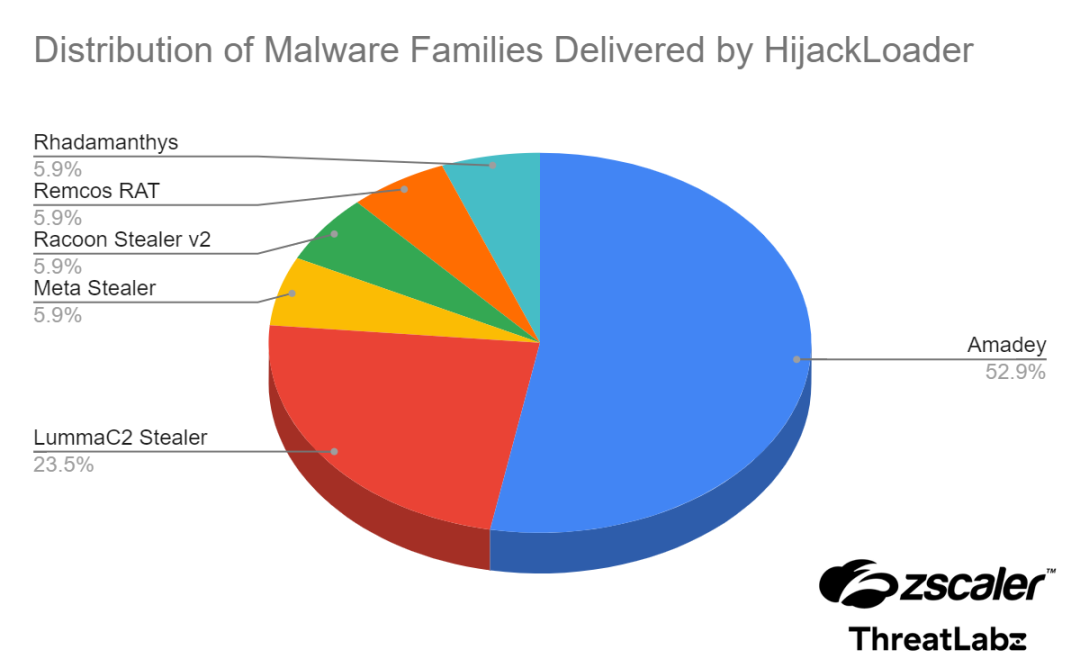
Furthermore, the research provides insights into the prevalence of various malware families distributed by HijackLoader, offering a glimpse into the ecosystem of threats facilitated by this loader.
The distribution statistics indicate a diverse range of payloads, emphasizing the loader’s role in the broader cybercrime landscape.
To aid in the fight against this evolving threat, the cybersecurity community has been provided with Indicators of Compromise (IOCs) and a list of MITRE ATT&CK techniques associated with HijackLoader.
These resources are crucial for detecting and mitigating the impact of this malware, as it continues to pose a significant challenge to cybersecurity defences worldwide.
The continuous evolution of HijackLoader underscores the dynamic nature of cyber threats and the need for ongoing vigilance and innovation in cybersecurity measures.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
The post HijackLoader Malware Attack Windows Via Weaponized PNG Image appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
Source: gbHackers
Source Link: https://gbhackers.com/hijackloader-malware/