DDoS (distributed denial-of-service) attacks have existed since the early days of the internet. While new tricks occasionally pop uplike leveraging certain vulnerabilities to amplify attacksthe core idea remains: overwhelming servers with more traffic than they can handle. Think of it as trying to push the ocean through a straw. When these attacks grow big, they can even disrupt internet providers themselves. Companies like Google and Cloudflare still battle these threats regularly, proving DDoS remains a serious issue even in 2025.
Historically, cybercriminals have targeted entire industries like airlines and banks, shutting the companies down until they paid. State-backed groups from countries like Russia and Iran also use DDoS attacks as weapons against their enemies.
Why Spend Money Before an Attack Happens?
Protecting against DDoS attacks matters because downtime means losing money or, for critical services, even worse consequences. But if your company hasn't been hit yet, why spend money on defenses? When should you start protecting yourself?
Thats where threat intelligence comes in handy. By looking at data and comparing trends, threat intelligence helps you decide if and when investing in DDoS defenses makes sense. It provides the insights to answer these questions for DDoS and any other cyber risk that may create one or more of the five risk impacts.
Smart Data Means Smart Decisions
Good decisions need good data. Recorded Future tracks thousands of DDoS attacks every day, giving you a clear picture of whos getting hit and how often. Pulling data from the Recorded Future API gives analysts useful analytics, like IP addresses targeted by attackers.
With this data, security teams can:
- Spot trends and predict who might be next
- Automate defenses and make faster decisions
- Better manage risk, knowing exactly when and how to invest
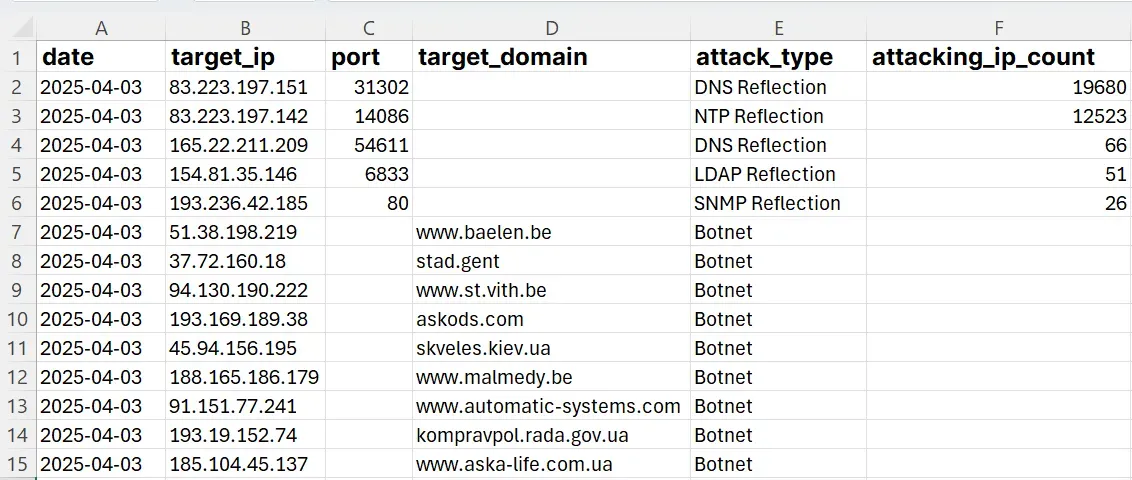 DDoS target list courtesy of Recorded Future
DDoS target list courtesy of Recorded Future
Who's Being Targeted?
Launching DDoS attacks isnt technically difficult. Someone with basic internet know-how can do it. But some attackers put more effort into it, building armies of infected devices known as botnets. One tool frequently used by pro-Russian hackers, called DDoSia, attacks different targets daily. By tracking whos getting hit most, businesses can better prepare their defenses.
For example, Ukraine currently faces heavy attacks due to geopolitical tensions. But finance and transportation companies in Europe are also frequent targets, suggesting broader threats.
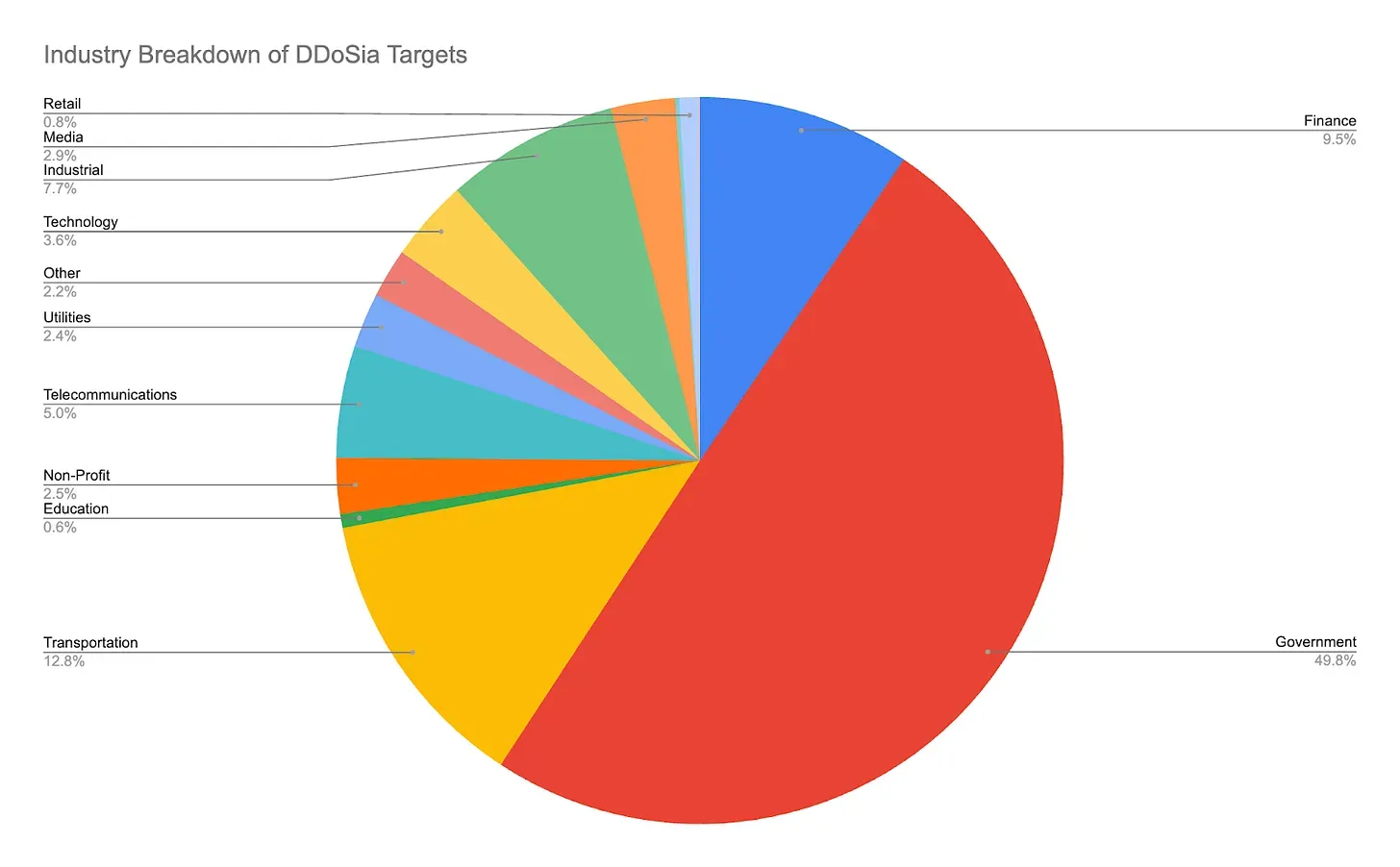 Ten months of DDoSia targets by industry, courtesy of Recorded Future
Ten months of DDoSia targets by industry, courtesy of Recorded Future
Thinking Bigger than Just Your Own Network
When CISOs arent considering crafting better risk management narratives for executive consumption, they are contemplating improving operational resilience. Denial of service attacks fall squarely in this category. The revolving questions dont stop with an organizations local network perimeter (if such a thing even exists anymore) but extend to partners, suppliers, and wider internet infrastructure (e.g., DNS and CDN providers).
More than ever, daily business and geopolitical events create a cascading effect of cyber impacts. DDoS is always a possibility. Recent attacks against X (Twitters hip rebrand) are a good reminder.
Key Decisions for Stronger DDoS Defense
The decisions that underpin DDoS defense and response correspond to organizational size, mission, footprint, regulatory compliance mandates, and resources. Here are some practical actions to consider:
- Partnering with your internet provider for fast response
- Using scrubbing centers to filter attack traffic
- Implementing challenge-response tests like CAPTCHAs
- Deploying cloud protections like AWS Shield
- Utilizing web application firewalls (WAF)
- Optimizing network setups (like load balancers and distributed data centers)
- Filtering traffic using firewalls and intrusion systems
- Relying on content delivery networks (CDNs)
- Using Anycast routing to protect DNS services
 Analytic contemplation courtesy of Gemini
Analytic contemplation courtesy of Gemini
Everyones a Target
Its tempting to think your business won't face a DDoS attack, especially if it's small or non-political. The reality? Anyone online can become a target for extortion or political agendas. That's why proactive intelligence is so valuableit helps security teams know when threats are getting closer and when its time to upgrade defenses.
As the frequency of DDoS attacks increases around certain industries or regions, it's essential to reassess and strengthen your own security controls accordingly. The closer these threats get, the more your organization should test their resilience. Said differently, as DDoS attack proximity moves closer to an organization, the operational disruption risk may, in parallel, need to move north on the resilience axis.
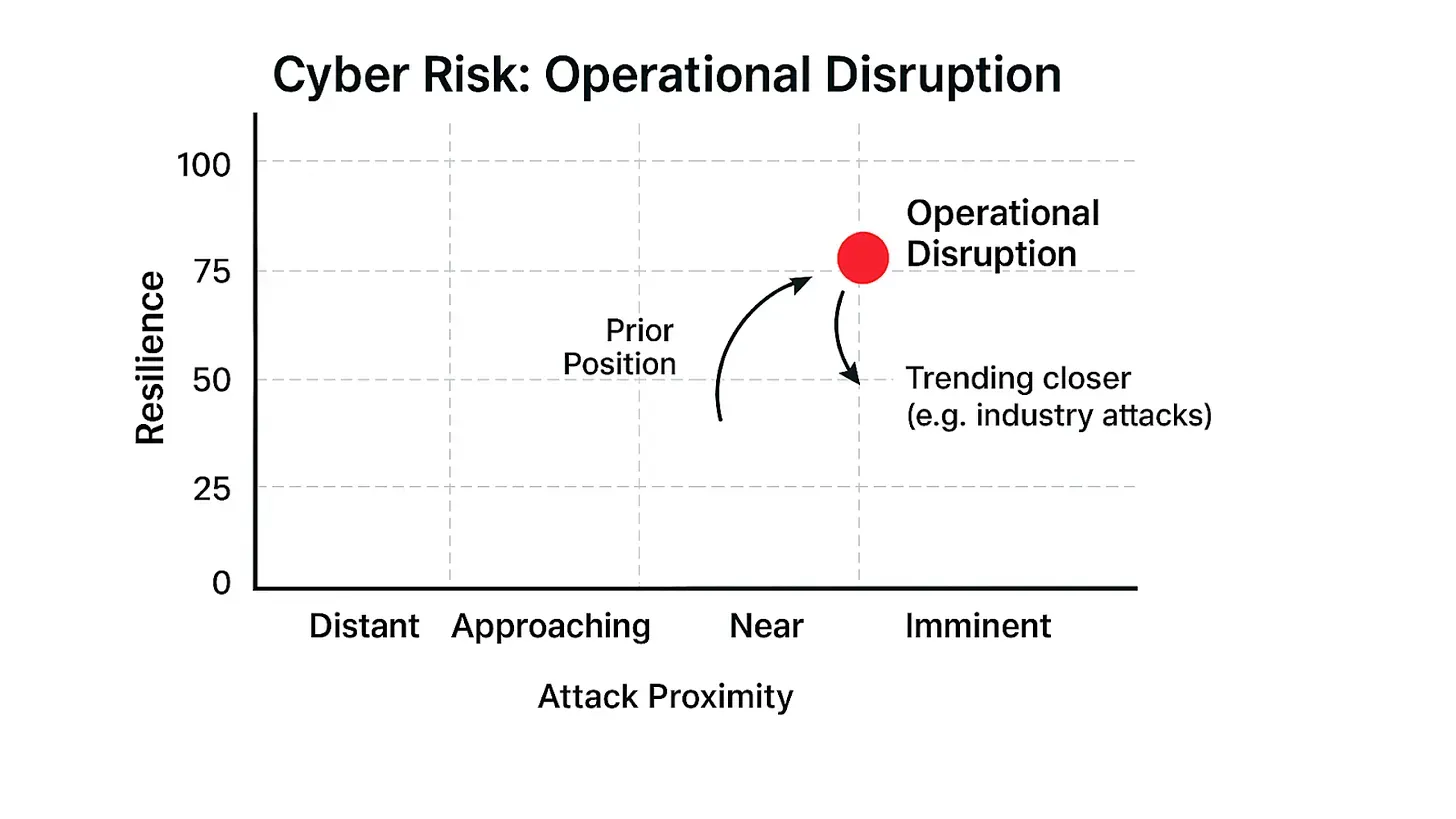 Risk Graph courtesy of ChatGPT
Risk Graph courtesy of ChatGPT
Staying One Step Ahead
DDoS attacks aren't going away, but they don't have to be a nightmare, either. Threat intelligence provides the clear insights needed to prepare and respond effectively. By using analytics wisely, organizations can invest smartly, build stronger defenses, and keep their operations running smoothly. When attacks creep closersay, spiking in your sector or geographysecond-order risks (like operational disruption) loom larger. Thats your cue to prioritize resilience, whether a CDN subscription or ISP speed-dial.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/blog/how-threat-intel-drives-smarter-security