Hundreds of thousands of clients who opted-in for a screen warranty were exposed when DNA Micro leaked data from its systems. The Cybernews research team found that DNA Micro, a California-based IT company, exposed the sensitive data of more than 820,000 customers due to a misconfiguration in its systems. The victims most affected by the […]
The post Californian IT company DNA Micro leaks private mobile phone data appeared first on Security Affairs.
Hundreds of thousands of clients who opted-in for a screen warranty were exposed when DNA Micro leaked data from its systems.
The Cybernews research team found that DNA Micro, a California-based IT company, exposed the sensitive data of more than 820,000 customers due to a misconfiguration in its systems.
The victims most affected by the data leak were those using the services of DNA Micro’s subsidiary company InstaProtek, which provides a screen warranty service. Other companies affected by the leak included screen protectors and phone case manufacturers, such as Liquipel and Otterbox, which used the warranty service.
The companies sell their products with a “You break it, we fix it” guarantee, taking responsibility for replacing the device’s screen in case damage occurs while using its products. DNA Micro gathered customer data and stored it on its systems to administer warranty services.
Unfortunately, it left the data – which included private information about devices and their owners – open to public access. The investigation by Cybernews shows that this was the case for at least 6 months.
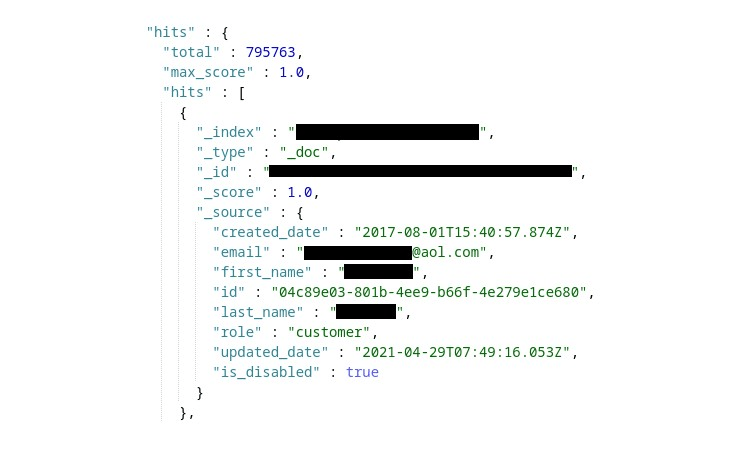
The leaked private data includes:
- Full names
- Addresses
- Phone numbers
- Email addresses
- Warranty claim status
- Phone models
- Purchase date
- International Mobile Equipment Identity (IMEI) numbers
- Store from which the item was purchased
- Cell carrier
The leak is hazardous, as threat actors could potentially attack individual devices and disrupt their services. Leaked private data can be used to create phishing campaigns and pose a threat to the company’s customers, potentially putting them at risk of “doxxing” and “swatting.” This is particularly concerning since sensitive information such as home addresses was also exposed.
The company was informed about the leak and has since fixed the issue. Cybernews reached out to DNA Micro for an official comment but has yet to hear back from them.
Companies that were affected by the leak:
- Instaprotek
- Otterbox
- Liquipel
- Health and Safety
- LJP Construction services
- AMP
- 23point5
- Intoto
Open Kibana instance to blame
On August 16th, the research team discovered three open Kibana instances containing sensitive data belonging to DNA Micro. The largest publicly accessible datastore was as big as 81GB.
Kibana is a dashboard interface for ElasticSearch, an open-source search and analytics engine. ElasticSearch instances store data that can be accessed and searched by ElasticSearch and Kibana.
These tools are designed to be used on local or private networks. Once the instance is exposed to the internet – without being secured by authentication – it’s accessible to anyone. This includes threat actors, who can easily exploit the leaked data.

Attacks could cause disruptions
Malicious actors could use a wide variety of attack vectors to exploit the leaked data. The exposure of IMEI numbers, along with personally identifiable data (PII) is particularly dangerous. IMEI is a unique number assigned to each mobile device and is used to identify a device on a mobile network.
Leaked IMEI numbers in the hands of threat actors can cause substantial damage. Attackers could use leaked data to replace IMEI numbers of stolen devices. If that happens, it can cause disruptions to the mobile service of the device.
Threat actors who might want to cause damage could also contact the cell carrier, reporting the allegedly stolen device to prevent it from connecting to that carrier’s mobile network and making the phone’s cell service unusable.
The leak also increases the risk of malware attacks, as exposed information about phone models could be exploited by threat actors. It allows them to roughly identify the age of the device, and the latest OS version supported, as well as what software it has installed by default.
Another piece of sensitive information that was leaked included customers’ phone numbers. Attackers could exploit customers’ numbers to send spam and conduct phishing campaigns. There’s also the danger of SIM swapping, and in rare cases, phone numbers could be used for tracking the user’s location. Not to forget, that phone numbers are a gateway to online information about the owner, as social media profiles containing phone numbers can easily be found.

Staying safe
Have you used DNA Micro services recently? Give a look at Cybernews’s recommendations at
https://cybernews.com/security/dna-micro-data-leak/
About the author: Paulina Okunytė Journalist ay Cybernews
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DNA Micro)
The post Californian IT company DNA Micro leaks private mobile phone data appeared first on Security Affairs.
Source: SecurityAffairs
Source Link: https://securityaffairs.com/152673/data-breach/dna-micro-data-leak.html